About direction,
Should we consider even more interruptions? Go deeper on what we have been exploring currently?
Should we start to consider other bigram 15, 19 transpositions options? It’s quite specific.
And last night I experienced a small eureka moment. A polyalphabetic cipher does not reduce bigrams more, than say, a regular homophonic cipher with randomized cycles. So I’m considering the 340 to be a kind of polyalphabetic cipher + the transposition element that introduced the bigram peaks at 15 and 19. Thus, he transposed the plaintext (perhaps in the same matter as smokie11) and then encoded it with some kind of polyalphabetic homophonic substitution scheme (upsetting the cycles).
The alternative is what we have been exploring so far. Transposition + randomization of cycles. Though it’s becoming more unlikely since we haven’t been able to solve it that way.
I combined all the plaintexts together and scored the words found in the result. Here they are:
https://docs.google.com/spreadsheets/d/ … sp=sharing
Longer words appear first. Within each length, words are in descending order of the combined score which is the product of the word’s relative frequency in the English language, and the number of times the word appears among the plain texts.
Thanks doranchak! That’s really cool, I’m gonna peer over it for a while. ![]()
20556_612_203_3167451.txt has "killing after":
taehefiledditeuso
nlameroingalcouli
pthethlicenrdcres
tedallameesevenan
iesintisnoniustra
denghistyprogrash
thlyimmifimrddopo
meoneongachilehim
umableddahasbeeid
elissoferribearto
rtclishylentoutin
gfucarpanandtunic
atalccsskillingaf
terbonalsohimsyou
rprstartheysiverb
allontoplesadfold
onalflantawatches
houldbeusoffanbut
thisveua
I wish I had a word-level n-gram matcher that could do fuzzy matches for phrases, using the number of edits and phrase frequencies as a way to rank them. I’d totally build one if I had the time. ![]()
Thanks doranchak! That’s really cool, I’m gonna peer over it for a while.
Caveat: I ran it on a concatenation of all the plaintexts, which means some words might appear but in fact are split between the end of one plaintext and the beginning of another.
About direction,
Should we consider even more interruptions? Go deeper on what we have been exploring currently?
Should we start to consider other bigram 15, 19 transpositions options? It’s quite specific.And last night I experienced a small eureka moment. A polyalphabetic cipher does not reduce bigrams more, than say, a regular homophonic cipher with randomized cycles. So I’m considering the 340 to be a kind of polyalphabetic cipher + the transposition element that introduced the bigram peaks at 15 and 19. Thus, he transposed the plaintext (perhaps in the same matter as smokie11) and then encoded it with some kind of polyalphabetic homophonic substitution scheme (upsetting the cycles).
The alternative is what we have been exploring so far. Transposition + randomization of cycles. Though it’s becoming more unlikely since we haven’t been able to solve it that way.
Although we don’t have a solution for the 340 at this point, I am still very excited about exploring transposition schemes and perhaps a polyalphabetic key that makes high count symbols look like they are 1:1 substitutes but they are not because they don’t appear to cycle with other symbols even though they cycle in multiple groups.
My suggestion is exploring the transposition idea until you are satisfied with the level of thoroughness weighed against the time that you feel comfortable spending on the idea.
I made the latest batch of messages with a spreadsheet, and have made several in the past by hand now. Making a transposed message like the one we have been working on would have been time consuming. I am almost thinking about doing one by hand to find out how long it takes and what it feels like. In any case, if that is what he did and he crossed off or checked off the original message plaintext as he was transposing, then there wouldn’t be any mistakes. But if he didn’t cross off or check off the original message plaintext as he was transposing, then any interruptions could easily have caused him to make some mistakes. In other words, if he took a break to answer the telephone, get a beer out of the fridge, or step out of the house for a few hours to go kill somebody, and he didn’t keep meticulous track of where he was during transposition, then there could easily be several errors in a 360 symbol message.
Have you tried to reverse the symbol order, which would also cause the period 15/19 bigram repeat phenomenon? 360, 359, 358 . . . 3, 2, 1.
You understand more about the results of your work than I do, so let me know what direction you want to go in. I will make messages to simulate whatever you want.
My suggestion is exploring the transposition idea until you are satisfied with the level of thoroughness weighed against the time that you feel comfortable spending on the idea.
Sure, I’m also in favor of sticking with just transposition for a while. Ideally I would like to make a small list or inventory of transposition schemes that relate to the bigram 15, 19 peak.
I’ve generated some basic versions (16) of the following interpretation. The 340 is split up in 15 or 19 parts (depending on the input orientation) without wrapping around the cipher. I’ve considered the normal, mirrored, flipped and reversed version of the cipher (17 by 20) as input and output with 15 or 19 parts accordingly. The reason why is because none of these variations diminish the bigram count.
Example image:

The following format is: input_output, with n=normal, m=mirrored, f=flipped, r=reversed. I plan to run this file through AZdecrypt with 5, 6 and 7-grams at an overkill number of random restarts and iterations. Because the cipher may also be polyalphabetic. I’ll get back with the results as they roll in.
Can anyone come up with something to make this scheme harder without reducing the bigram counts too much? Without wrapping around the cipher, I want to keep that for later. Changing the initial offset should be trivial but what if Zodiac made some errors?
Bigram counts:
Input: normal
340n_b19n: 37
340n_b19m: 34
340n_b19f: 34
340n_b19r: 37
Input: mirrored
340m_b15n: 41
340m_b15m: 41
340m_b15f: 41
340m_b15r: 41
Input: flipped
340f_b15n: 41
340f_b15m: 38
340f_b15f: 38
340f_b15r: 41
Input: reversed
340r_b19n: 37
340r_b19m: 35
340r_b19f: 35
340r_b19r: 37
Input mirrored and flipped have the highest bigram counts, this relates to the higher peak at 15 we’ve talked about.
AZdecrypt file, go ahead if you like:
Update: corrected a string in the file.
Update 2: corrected another string in the file.
results_sub_directory=340_test cipher_information=340n_b19n H+M8|CV@K+l#2E.B) >EB+*5k.L-RR+4>f| pMR(UVFFz9z/JNbVM )|D>#Z3P>Ldl5||.U qLFHpOGp+2|<Ut*5c ZG+kNl%WO&D(MVE5F V52+dp^D(+4(G++|T B4-R)WkVW)+k#2b^D 4ct+cW<SPYLR/5J+J YM(+|TC7zk.#Kp+fZ +B.;+c+ztZ|<z28Kj ROp+8y.LWBO1*H_Rq #2pb&RB31c_8LKJ9^ %OF7TBlXz6PYATfSM F;+B<MFG1BCOO|G)p +l2_cFKzF*K<SBK2B pzOUNyBO6N:(+H*;d y7t-cYAy29^4OFT-+ N:^j*Xz6-<Sf9pl/C pclddG+4Ucy5C^W(c cipher_information=340n_b19m )B.E2#l+K@VC|8M+H |f>4+RR-L.k5*+BE> MVbNJ/z9zFFVU(RMp U.||5ldL>P3Z#>D|) c5*tU<|2+pGOpHFLq F5EVM(D&OW%lNk+GZ T|++G(4+(D^pd+25V D^b2#k+)WVkW)R-4B J+J5/RLYPS<Wc+tc4 Zf+pK#.kz7CT|+(MY jK82z<|Ztz+c+;.B+ qR_H*1OBWL.y8+pOR ^9JKL8_c13BR&bp2# MSfTAYP6zXlBT7FO% p)G|OOCB1GFM<B+;F B2KBS<K*FzKFc_2l+ d;*H+(:N6OByNUOzp +-TFO4^92yAYc-t7y C/lp9fS<-6zX*j^:N c(W^C5ycU4+Gddlcp cipher_information=340n_b19f pclddG+4Ucy5C^W(c N:^j*Xz6-<Sf9pl/C y7t-cYAy29^4OFT-+ pzOUNyBO6N:(+H*;d +l2_cFKzF*K<SBK2B F;+B<MFG1BCOO|G)p %OF7TBlXz6PYATfSM #2pb&RB31c_8LKJ9^ ROp+8y.LWBO1*H_Rq +B.;+c+ztZ|<z28Kj YM(+|TC7zk.#Kp+fZ 4ct+cW<SPYLR/5J+J B4-R)WkVW)+k#2b^D V52+dp^D(+4(G++|T ZG+kNl%WO&D(MVE5F qLFHpOGp+2|<Ut*5c )|D>#Z3P>Ldl5||.U pMR(UVFFz9z/JNbVM >EB+*5k.L-RR+4>f| H+M8|CV@K+l#2E.B) cipher_information=340n_b19r c(W^C5ycU4+Gddlcp C/lp9fS<-6zX*j^:N +-TFO4^92yAYc-t7y d;*H+(:N6OByNUOzp B2KBS<K*FzKFc_2l+ p)G|OOCB1GFM<B+;F MSfTAYP6zXlBT7FO% ^9JKL8_c13BR&bp2# qR_H*1OBWL.y8+pOR jK82z<|Ztz+c+;.B+ Zf+pK#.kz7CT|+(MY J+J5/RLYPS<Wc+tc4 D^b2#k+)WVkW)R-4B T|++G(4+(D^pd+25V F5EVM(D&OW%lNk+GZ c5*tU<|2+pGOpHFLq U.||5ldL>P3Z#>D|) MVbNJ/z9zFFVU(RMp |f>4+RR-L.k5*+BE> )B.E2#l+K@VC|8M+H cipher_information=340m_b15n dEB+*5k.L(MVE5FV5 2c+ztZ2H+M8|CV@K< Ut*5cZG|TC7zG)pcl ddG+4dl5||.UqLcW< STfN:^j*Xz6-z/JNb VM)R)WkLKJy7t-cYA y-RR+4>f|p+dp1*HB pzOUNyBO+l#2E.B)+ kN|<z2p+l2_cFKUcy 5C^W(cFHk.#KSMF;+ B<MF<Sf9pl/C|DPYL R/9^%OF7TB29^4OFT -+MVW)+k_Rq#2pb&R 6N:(+H*;>^D(+4(8K jROp+8zF*K<SBKl%W O&Dp+fZ+B.;+G1BCO O|pOGp+2|5J+JYM(+ lXz6PYA>#Z3P>L#2b ^D4ct+B31c_8R(UVF Fz9G++|TB4-y.LWBO cipher_information=340m_b15m 5VF5EVM(L.k5*+BEd <K@VC|8M+H2Ztz+c2 lcp)Gz7CT|GZc5*tU <WcLqU.||5ld4+Gdd bNJ/z-6zX*j^:NfTS AYc-t7yJKLkW)R)MV BH*1pd+p|f>4+RR-y +)B.E2#l+OByNUOzp ycUKFc_2l+p2z<|Nk +;FMSK#.kHFc(W^C5 LYPD|C/lp9fS<FM<B TFO4^92BT7FO%^9/R R&bp2#qR_k+)WVM+- K8(4+(D^>;*H+(:N6 W%lKBS<K*Fz8+pORj OCB1G+;.B+Zf+pD&O +(MYJ+J5|2+pGOp|O b2#L>P3Z#>AYP6zXl FVU(R8_c13B+tc4D^ OBWL.y-4BT|++G9zF cipher_information=340m_b15f Fz9G++|TB4-y.LWBO ^D4ct+B31c_8R(UVF lXz6PYA>#Z3P>L#2b O|pOGp+2|5J+JYM(+ O&Dp+fZ+B.;+G1BCO jROp+8zF*K<SBKl%W 6N:(+H*;>^D(+4(8K -+MVW)+k_Rq#2pb&R R/9^%OF7TB29^4OFT B<MF<Sf9pl/C|DPYL 5C^W(cFHk.#KSMF;+ kN|<z2p+l2_cFKUcy pzOUNyBO+l#2E.B)+ y-RR+4>f|p+dp1*HB VM)R)WkLKJy7t-cYA STfN:^j*Xz6-z/JNb ddG+4dl5||.UqLcW< Ut*5cZG|TC7zG)pcl 2c+ztZ2H+M8|CV@K< dEB+*5k.L(MVE5FV5 cipher_information=340m_b15r OBWL.y-4BT|++G9zF FVU(R8_c13B+tc4D^ b2#L>P3Z#>AYP6zXl +(MYJ+J5|2+pGOp|O OCB1G+;.B+Zf+pD&O W%lKBS<K*Fz8+pORj K8(4+(D^>;*H+(:N6 R&bp2#qR_k+)WVM+- TFO4^92BT7FO%^9/R LYPD|C/lp9fS<FM<B +;FMSK#.kHFc(W^C5 ycUKFc_2l+p2z<|Nk +)B.E2#l+OByNUOzp BH*1pd+p|f>4+RR-y AYc-t7yJKLkW)R)MV bNJ/z-6zX*j^:NfTS <WcLqU.||5ld4+Gdd lcp)Gz7CT|GZc5*tU <K@VC|8M+H2Ztz+c2 5VF5EVM(L.k5*+BEd cipher_information=340f_b15n >;*H+(:N6R&bp2#qR _k+)WVM+-TFO4^92B T7FO%^9/RLYPD|C/l p9fS<FM<B+;FMSK#. kHFc(W^C5ycUKFc_2 l+p2z<|Nk+)B.E2#l +OByNUOzpBH*1pd+p |f>4+RR-yAYc-t7yJ KLkW)R)MVbNJ/z-6z X*j^:NfTS<WcLqU.| |5ld4+Gddlcp)Gz7C T|GZc5*tU<K@VC|8M +H2Ztz+c25VF5EVM( L.k5*+BEdOBWL.y-4 BT|++G9zFFVU(R8_c 13B+tc4D^b2#L>P3Z #>AYP6zXl+(MYJ+J5 |2+pGOp|OOCB1G+;. B+Zf+pD&OW%lKBS<K *Fz8+pORjK8(4+(D^ cipher_information=340f_b15m Rq#2pb&R6N:(+H*;> B29^4OFT-+MVW)+k_ l/C|DPYLR/9^%OF7T .#KSMF;+B<MF<Sf9p 2_cFKUcy5C^W(cFHk l#2E.B)+kN|<z2p+l p+dp1*HBpzOUNyBO+ Jy7t-cYAy-RR+4>f| z6-z/JNbVM)R)WkLK |.UqLcW<STfN:^j*X C7zG)pclddG+4dl5| M8|CV@K<Ut*5cZG|T (MVE5FV52c+ztZ2H+ 4-y.LWBOdEB+*5k.L c_8R(UVFFz9G++|TB Z3P>L#2b^D4ct+B31 5J+JYM(+lXz6PYA># .;+G1BCOO|pOGp+2| K<SBKl%WO&Dp+fZ+B ^D(+4(8KjROp+8zF* cipher_information=340f_b15f *Fz8+pORjK8(4+(D^ B+Zf+pD&OW%lKBS<K |2+pGOp|OOCB1G+;. #>AYP6zXl+(MYJ+J5 13B+tc4D^b2#L>P3Z BT|++G9zFFVU(R8_c L.k5*+BEdOBWL.y-4 +H2Ztz+c25VF5EVM( T|GZc5*tU<K@VC|8M |5ld4+Gddlcp)Gz7C X*j^:NfTS<WcLqU.| KLkW)R)MVbNJ/z-6z |f>4+RR-yAYc-t7yJ +OByNUOzpBH*1pd+p l+p2z<|Nk+)B.E2#l kHFc(W^C5ycUKFc_2 p9fS<FM<B+;FMSK#. T7FO%^9/RLYPD|C/l _k+)WVM+-TFO4^92B >;*H+(:N6R&bp2#qR cipher_information=340f_b15r ^D(+4(8KjROp+8zF* K<SBKl%WO&Dp+fZ+B .;+G1BCOO|pOGp+2| 5J+JYM(+lXz6PYA># Z3P>L#2b^D4ct+B31 c_8R(UVFFz9G++|TB 4-y.LWBOdEB+*5k.L (MVE5FV52c+ztZ2H+ M8|CV@K<Ut*5cZG|T C7zG)pclddG+4dl5| |.UqLcW<STfN:^j*X z6-z/JNbVM)R)WkLK Jy7t-cYAy-RR+4>f| p+dp1*HBpzOUNyBO+ l#2E.B)+kN|<z2p+l 2_cFKUcy5C^W(cFHk .#KSMF;+B<MF<Sf9p l/C|DPYLR/9^%OF7T B29^4OFT-+MVW)+k_ Rq#2pb&R6N:(+H*;> cipher_information=340r_b19n +-TFO4^92yAYc-t7y d;*H+(:N6OByNUOzp B2KBS<K*FzKFc_2l+ p)G|OOCB1GFM<B+;F MSfTAYP6zXlBT7FO% ^9JKL8_c13BR&bp2# qR_H*1OBWL.y8+pOR jK82z<|Ztz+c+;.B+ Zf+pK#.kz7CT|+(MY J+J5/RLYPS<Wc+tc4 D^b2#k+)WVkW)R-4B T|++G(4+(D^pd+25V F5EVM(D&OW%lNk+GZ c5*tU<|2+pGOpHFLq U.||5ldL>P3Z#>D|) MVbNJ/z9zFFVU(RMp |f>4+RR-L.k5*+BE> )B.E2#l+K@VC|8M+H c(W^C5ycU4+Gddlcp C/lp9fS<-6zX*j^:N cipher_information=340r_b19m y7t-cYAy29^4OFT-+ pzOUNyBO6N:(+H*;d +l2_cFKzF*K<SBK2B F;+B<MFG1BCOO|G)p %OF7TBlXz6PYATfSM #2pb&RB31c_8LKJ9^ ROp+8y.LWBO1*H_Rq +B.;+c+ztZ|<z28Kj YM(+|TC7zk.#Kp+fZ 4ct+cW<SPYLR/5J+J B4-R)WkVW)+k#2b^D V52+dp^D(+4(G++|T ZG+kNl%WO&D(MVE5F qLFHpOGp+2|<Ut*5c )|D>#Z3P>Ldl5||.U pMR(UVFFz9z/JNbVM >EB+*5k.L-RR+4>f| H+M8|CV@K+l#2E.B) pclddG+4Ucy5C^W(c N:^j*Xz6-<Sf9pl/C cipher_information=340r_b19f C/lp9fS<-6zX*j^:N c(W^C5ycU4+Gddlcp )B.E2#l+K@VC|8M+H |f>4+RR-L.k5*+BE> MVbNJ/z9zFFVU(RMp U.||5ldL>P3Z#>D|) c5*tU<|2+pGOpHFLq F5EVM(D&OW%lNk+GZ T|++G(4+(D^pd+25V D^b2#k+)WVkW)R-4B J+J5/RLYPS<Wc+tc4 Zf+pK#.kz7CT|+(MY jK82z<|Ztz+c+;.B+ qR_H*1OBWL.y8+pOR ^9JKL8_c13BR&bp2# MSfTAYP6zXlBT7FO% p)G|OOCB1GFM<B+;F B2KBS<K*FzKFc_2l+ d;*H+(:N6OByNUOzp +-TFO4^92yAYc-t7y cipher_information=340r_b19r N:^j*Xz6-<Sf9pl/C pclddG+4Ucy5C^W(c H+M8|CV@K+l#2E.B) >EB+*5k.L-RR+4>f| pMR(UVFFz9z/JNbVM )|D>#Z3P>Ldl5||.U qLFHpOGp+2|<Ut*5c ZG+kNl%WO&D(MVE5F V52+dp^D(+4(G++|T B4-R)WkVW)+k#2b^D 4ct+cW<SPYLR/5J+J YM(+|TC7zk.#Kp+fZ +B.;+c+ztZ|<z28Kj ROp+8y.LWBO1*H_Rq #2pb&RB31c_8LKJ9^ %OF7TBlXz6PYATfSM F;+B<MFG1BCOO|G)p +l2_cFKzF*K<SBK2B pzOUNyBO6N:(+H*;d y7t-cYAy29^4OFT-+
The pattern looks like the stripes on a candy cane.
Are you satisfied with your analysis of the rectangular 19 row transposition scheme? I was thinking last night that you may want to work on the "candy cane" transposition soon.
I have to think about a comparison between the candy cane and 19 row rectangle. If we un-transpose them, are we not reconstructing the original order of plaintext either way? Maybe not and I will ponder this scheme a bit. If you want a candy cane message with some missing plaintext or whatever, let me know. I could make a tracing map and then we could compare the candy cane and 19 row versions if you want. Or whatever.
Are you satisfied with your analysis of the rectangular 19 row transposition scheme? I was thinking last night that you may want to work on the "candy cane" transposition soon.
I thought about it, the main difficulty of your scheme + errors are the misalignments. So only the misalignments need to fixed rather than every character, this way I could add much more depth to the test (consider more errors). The problem (I think) is that a large number of errors are not in favor of a strong peak at 19, so I’m a bit reluctant.
You may decide. I think it would perhaps be better to go broad first, make a list/inventory of all transpositions leading to a 15, 19 bigram peak. Do a few good tests for each transposition and move on and then later come back to things that were interesting. Gain the best possible understanding of the problem.
I have to think about a comparison between the candy cane and 19 row rectangle. If we un-transpose them, are we not reconstructing the original order of plaintext either way? Maybe not and I will ponder this scheme a bit. If you want a candy cane message with some missing plaintext or whatever, let me know. I could make a tracing map and then we could compare the candy cane and 19 row versions if you want. Or whatever.
It’s a good question. It should not be the same because my interpretation is diagonal and yours is vertical but an in-depth tracing map may not hurt to gain a better understanding. I would like to see it!
I will work on some simple comparisons soon. We should have a small library of transposition schemes with tracing maps for comparison. I will start on a candy cane map starting at position 1 with no wraparound tonight unless you change your mind and tell me that you want something else.
Ok smokie,
I’ve done a bit of testing myself and both schemes are identical when considering the cipher in a 17 by 19 grid (length 323). And with other message lengths misalignments between the 2 start to occur. My interpretation keeps its period (so to say) while yours starts to leak into another period. And by all means go ahead with your comparison.
Update: I find it hard to understand why the 340 is not solving under our current hypotheses. The next cipher has the bigram 15>19 scheme, I also randomized the cycles by 20% but it’s still WAY more cyclic than the 340 according to my primary measurement while the non-repeats score is quite a bit lower…
/NaAhDMBC*O[)Y07h !]"_<h-.P,'g$*#@L aK64(!FKSWeJ)N1D/ ^I&0<XKNd+;$7)Ue <4a?afKD=ah9C13#4 h/h?G9a>,E%L+ghh[ F0AOOM"(dTHYR-O9h hh@2W.P2h$&!*a)h< h^0hDCfGaR1eXB_;6 h,7$27g'YH>F(!1h4 KE%#S/)UEA^?XHaTD =>C[3<aL2=Y$@J1*d *"_#'KFfG]0[L-.,P hAgd+eIhh&04h++(W M="H6(aO7h>fh!"^9 ?]=?S>hXG)e-9%hOR 12ETA+.NhUP/&20;7 <YBdK[@^IL"e1/CFd JfhM_>-ID'C6S%>,@ e<dg.]9=eBJP'h&$N
I am not clear by what you mean when you say that you randomized the cycles.
In any case, I am wondering if we should take a look at the statistical significance of the period 19 bigram repeats. You did 1 million shuffles and got 1, is that correct?
Have you considered writing a program that creates messages. You could randomly choose from your 100 plaintext library and then randomly populate the key with symbols. Maybe have some variable for the flatness of the key. Then encode. Something to that effect.
Do that 1 million times and see what happens. Has anyone ever done that before (probably)?
I am still pretty convinced about transposition. But I will think about it and continue my comparisons between 17×19 and candy cane. They are the same depending on where you start and the direction that you go in.
I just meant I added a 20% chance to pick a homophone at random rather than cycling it during the encoding.
Yes, and the mirrored peak should be even rarer. I have unearthed new evidence that the 340 is such a transposition scheme and that something is wrong/different also (misalignment).
In the following image I stacked a 340 character version of the 408 with a bigram 19 and 15 scheme (the interpretation I talked about) versus the 340. Please note that the image is showing bigram repeats at various periods. The x-axis being the period and the y-axis being the frequency and the different colors are the orientations. Most notably red is normal and green is mirrored. I’ve marked 1, 2 and 3 on each of them. 1 is the main scheme with it’s appropriate peak, 2 is its mirrored peak (which is typically a little less pronounced) and 3 is a reflection (what I’ve come to call it) at double the period of the main scheme. Guess what, the 340 compares very well with the 408 bigram 15 scheme I introduced but there is a small discrepancy. The relfection (number 3) is at 29 instead of 30.
Based on this I’d like to postulate the following: the 340 is a bigram 15 scheme (hence it reflection at 29). But is somehow misaligned (perhaps a mix between 14 and 15?), which causes the reflection to sit at 29 instead of 30. I don’t think it can get much clearer than this, the evidence is sitting right in front of us.

Interesting! It makes me curious if periodic trigrams could also be found to correlate to the periodic bigram peaks. Or, instead of trigrams, maybe periodic repeating fragments can also be found at the same periods where bigrams are peaking (the periodic equivalent of, say, the A?B?C type patterns where "?" can be any symbol).
If those kinds of patterns also peak at the same periods, maybe it would be a type of confirmation of the scheme.
You guys might be talking about this. I was recently looking for period 19 trigrams. I didn’t find any, but was looking by "eye" when tired and not by computer.
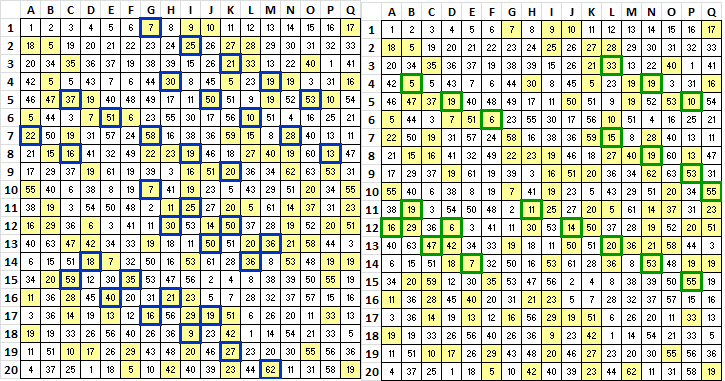
The symbols in a lot of the period 15/19 bigram repeats show up in diagonal rows. The yellow shaded cells are the cells with period 15/19 bigram repeat symbols. The heavy bordered cells are the ones that line up in diagonal rows. Two separate images shown for clarity.
EDIT: I predict that there will be more than a few good examples where you have ABC and ABD and C and D cycle together. Or ABCD and ABED and C and E cycle together. There will be stuff like that because there is a message in there and C and D map to the same plaintext. Or C and E map to the same plaintext. Etc.