I have used my current motivation to continue working on my as yet unpublished solver. It is not as good as AZDecrypt by Jarlve, but it works in general and can solve homophonic encryptions. Many thanks at this point to Jarlve, who gave many valuable tips and answered my questions.
If you are not interested in the details and would rather test the Peek-a-boo built-in version, you can find instructions here: viewtopic.php?f=81&t=3255&start=50#p63691
The solver is a console application written in C++ that runs as a server. The whole thing is based on the zeromq-library ( http://zeromq.org ).
After startup, the solver loads the ngrams (5-grams) and waits for network packets. Send the ciphertext to the solver via the corresponding IP and port and you will get the plain text and the score as a response. Of course you can also start the solver locally on your own computer (localhost).
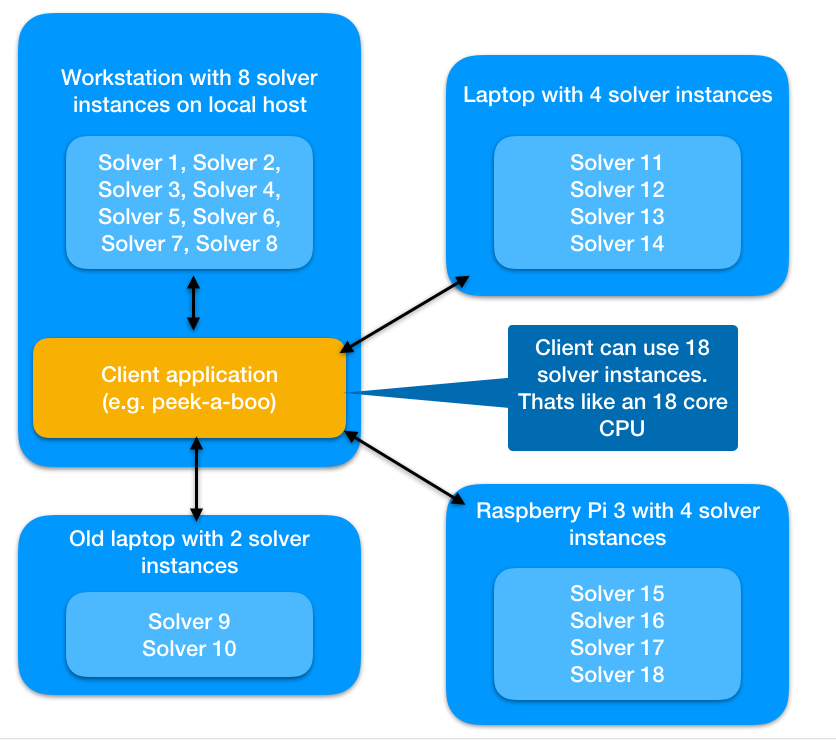
The advantage is that you theoretically could start as many solvers as you like at the same time (so far, however, only one instance is possible because the IP is set to localhost). The more threads the CPU supports, the more solvers running simultaneously make sense. For example, you could run four solvers on your own computer and many more on all available computers and laptops in the household. Let’s say you want to test thousands of transposition variants, then you could send the variations one by one to each of these solvers (queue). As soon as one of the solvers sends the result, you can send it another cipher. The available computing power is therefore not limited to a working PC, but can be scaled to any size. The following picture show how it will work in the future:
In the picture above 18 solvers are running simultaneously. This makes it possible, for example, to have 18 different transposition ideas evaluated in one go. Alternatively, you might send the same ciphertext to all 18 solvers and use the result with the best score. It’s like having a CPU with 18 threads! As mentioned, the solver is currently limited to a single instance, since the IP address is fixed.
I am considering publishing the solver as an open source project so that interested people can contribute to it. Until then, I will release it only in a package together with Peek-a-boo. I integrated the solver into Peek-a-boo and added a "solve" button. How to use the new feature is described in the thread viewtopic.php?f=81&t=3255&start=50#p63691.
The solver does not have as many functions as AZDecrypt and is also not as advanced. The advantage is that the workload can be distributed to any number of computers and that you can access the solver directly using your own tools. It is therefore not a competition to AZDecrypt, but a different approach.
If you like to use the solver as a stand alone tool independent of Peek-a-boo, you can do this in any programming language. Simply start TheRaccoon.exe from the Peek-a-boo download and send an encrypted text via 127.0.0.1:5555. You will receive the plaintext and a score. This requires the zeromq library. Simple client examples for common programming languages can be found here:
Java: http://zguide.zeromq.org/java:hwclient
C++: http://zguide.zeromq.org/cpp:hwclient
C#: http://zguide.zeromq.org/cs:hwclient
Python: http://zguide.zeromq.org/py:hwclient
Note: If you start the solver, Windows asks for network permissions. This is necessary because it communicates via network protocols. (Some antivirus programs recognize this as a threat)
Translated with http://www.DeepL.com/Translator
This is a great idea and project Largo!
Are you thinking about building some sort of beowulf cluster?
Are you thinking about building some sort of beowulf cluster?
I’ve never heard this term and therefore looked it up on Wikipedia. Yes, the concept is very similar. In theory, however, computers can also be integrated into the cluster via the Internet. Not tried it yet, but should work. A bit like Seti@Home.
https://en.wikipedia.org/wiki/SETI@home
In theory, however, computers can also be integrated into the cluster via the Internet. Not tried it yet, but should work. A bit like Seti@Home.
That would be amazingly cool.
ZODIAC@home
![]()
ZODIAC@home

Yeah, I had the that idea too ![]()
If you keep dreaming about it, you’ll end up with a kind of "Zodiac@Home" (spooky name, I know…), which works exactly like Seti@Home. =)
viewtopic.php?f=81&t=3198&p=57397&hilit=seti#p57397
Nice work, Largo! It’s really exciting that you made it so scalable.
Nice work, Largo! It’s really exciting that you made it so scalable.
Thank you! I hope I can post an update soon which allows clustering.
I’ll plan to implement a Vigenere solver. Currently I am very enthusiastic.
Can somebody please do me a favor? I need 2-3 test ciphers with the following criteria:
Step 1: An valid text in english. 340 letters.
Step 2: Perform a transposition. For example period n or diagonal or something else.
Step 3: Encrypt with classical Vigenere. Please use a maximum of 8 characters for the password for now.
Optional: Two transposition steps in Step 2
Should I still be able to decipher that now? We’ll see ![]()
Thank you in advance.
Can somebody please do me a favor? I need 2-3 test ciphers with the following criteria:
miichgokftwiumhll resyhfasrhvroaarg dpnrlylrizspdrigy sgzolrfgbcnfzumrv rrsrrbuzrsjmzffui rdvgwzizkipojottf mrclacvpynutmfoer uqecrbgtkrkrtuuhy gvagcyrkwsovuizil mplciibmgdtcnmett ecvopserumcbxavet kozltxuizbizoltxg vnixgbewliimaytfs hikcwuikwstbzwaeu msqtjtmcgmtceyryw yefowphjuszexuvzw ctosojtftilggyygk ilaksoyluodovnuhz oinmysvyglijyspaf nicerzrtognbyntxa xesgfshxstokjesem wbxeldktchkgdvnia wzxdrkepouocvtbcv ypssuiyzkjpuzvhot fxcjilqzbgczuecno ofzsoqreloggxbipp wnflrojofgjpvxoeb njlfjgydntymepwci fxfnosfrijvkfzczx dhxmswgcdoyqdokfd vrtysotlvojprxndo ntdwnxfrujwuoqwqp vdcubxhzzpkozeuud lgniroyiphogewubd ssjthyiobztppxddr ydzimbdkyfcsgpyso osaoitvobebkbssyx lrssurxbtokefsktt azfpbzztsocdwymcg kuwhnwxvumhugtupu
Thank you Jarlve!
First one: Monkey Island =)
Working on second one…
@Jarlve:
Second cipher is about Kirk, correct?
Thank you Jelberg!
Can’t Take My Eyes off You – Frankie Valli and The 4 Seasons. Keyword "excorcist".
Well done Largo. Here’s another:
crclbwlacmagydrhg mbawgutsgfmqgqwgq fxhnctljqzujaikvo cmtnjtvgaxyjgohpm hdotnqxolffdgxgvq skglgsrokmbcgnfvy nftgtgmyrfvqulytw tunffwamcqctlfkwf yluzehqlfutvufcmy ygakqvhjqscrkufkj kkbysnokmhlaicgkb idyfttlhwjuonbyjf skphyaqsvsoqsvdvf xfnuseqislugfawas edjlbivuhujlazcwg ghcwvcojknjpzglmm hcrvdawlcdqmtuskw qcrywjhvdlyfpwgwg jkgfvblwggctrhckj pvqxemkrcyflwcbuy
@Jarlve:
Another Lucas Arts Game: The Dig.
To put the cards on the table: That’s not entirely my own work. I use various tools, including AZDecrypt. For the decoding of Vigenere I have researched the last days a lot and looked at different algorithms. I came across a page with a different approach than most others. There, the Kasiski or Friedman test is not used, but ngrams. The solver on the linked page is outstanding.
https://www.guballa.de/vigenere-solver
Since I’m just examining other ciphers, I’ve worked a lot with the Guballa solver. I noticed that the keyword is almost always determined, even if the cipher is transposed. That made me wonder. Maybe that’s a known phenomenon you already aware of. At least it amazes me. If someone knows the reason why the keyword can also be determined with transposed ciphers, then I am curious. Maybe I’m just amazed at something that’s common knowledge.
I will try to implement the algorithm used on the linked page myself and integrate it into my solver.
Here is how the solver works:
https://www.guballa.de/implementierung- … re-solvers
(Only availabe in German, you may try to translate it with http://www.deepl.com/Translator )
Translated with http://www.DeepL.com/Translator
Since I’m just examining other ciphers, I’ve worked a lot with the Guballa solver. I noticed that the keyword is almost always determined, even if the cipher is transposed. That made me wonder. Maybe that’s a known phenomenon you already aware of. At least it amazes me. If someone knows the reason why the keyword can also be determined with transposed ciphers, then I am curious. Maybe I’m just amazed at something that’s common knowledge.
That solver indeed works really well. I have played around with it before. It is very likely also using the chi-squared statistic to determine the keyword. That is what you are looking for and it only works on plaintext ciphers.
https://en.wikipedia.org/wiki/Chi-squared_test
http://practicalcryptography.com/crypta … statistic/
Thanks for the information Jelberg and Jarlve. I’ll take a closer look. I am excited!
That solver indeed works really well. I have played around with it before. It is very likely also using the chi-squared statistic to determine the keyword. That is what you are looking for and it only works on plaintext ciphers.
Nope, the solver does not use any chi-squared statistic method. It solely relies on ngrams. This is true for determining the key length as well as finding the best key.