**[ I probably didn’t approach this topic in an organized and approachable way so let me try and explain what I’m doing here. What it boils down to is this: I’m personally convinced that a physical key was used to create the 408, but I didn’t start out that way. I needed to test it. I still need to test it. That said, I don’t think that is an inherently obvious extrapolation. As an example, it would be possible, though harder, to look back at your cipher during encryption and copy substitutions you had already made for certain plaintext letters. I suspect, however, this would be extremely difficult unless you had a very organized and well structured workflow.
Now we know the author screwed it up, but why? I didn’t know. Can I find out why? Maybe if I pick apart the way in which he screwed it up, sort of the way you pick apart debris in a plane crash, I can reconstruct what probably happened. Having done that, I’m much more comfortable with the idea that there way a physical key he used to encipher the text. I’m less comfortable with the idea that, in his key, the letters I examined were physically proximate. However, I think it is a very credible explanation for the mistakes were made. In support of this conclusion, I offer the work I did below.
Assuming this is a reasonable explanation, what we now have in front of us is not only the symbols he used for each letter, but also the symbols he used for letters that were directly adjacent to one another in his physical key. What we can then do with that information is evaluate it. We can extrapolate common features and patterns about how the author made his cipher. In the course of evaluating the potential resource I now have in front of me as a result of my analysis, It occurs to me that the groupings of this key share features with the keys of a typewriter.
That quite possibly means he is using a typewriter in some capacity to create this cipher, whether at one point in his process or, potentially, more. That is the gist of what I’m trying to explore in this topic. I’m trying to data mine. ]
Hi all,
New to the forum but have been following for the past month or so.
Let me cut to the point; I’m aware that there has been some discussion related to mistakes by the author of z408 and, in frustration at the opaqueness of z340, I decided to dig into the original cipher to see if I could learn anything about the author and his process from patterns in his mistakes. This, in turn, led me to build a spreadsheet charting the cycles of four plaintext letters [O, A, S and T] and their corresponding homophones. I think this topic has been explored on some level before, but I’m not sure if anyone is aware of an analysis of this type before and so I thought I might share my results to see if anyone has useful input to offer (including whether this is probably a waste of time).
Just a quick primer to orient you to the following image; For each letter, I assumed that the order in which their associated symbols appear in the cipher was related to their relative position in the original encryption key. Then I labeled each symbol according to the plaintext letter they are substituted for and the order in which they are first substituted [ in other words for plaintext "S", ‘F’ becomes S1, ‘Square with dot’ becomes S2, ‘K’ becomes S3, etc. ] Then I mapped out all the instances where the symbols appear in three timelines corresponding to the three sections by which the cipher was originally distributed and then, where mistakes were made, I compared the homophones corresponding to that position in the encryption cycle to other plaintext letters and their related cycle positions. By doing this, it’s possible to see how the habits of the author caused particular mistakes to occur. It’s pretty simple when you see it. I’ve linked an image here:
EDIT: And if there’s a better place to host images/files like Google Drive or whatever let me know. You’ll probably have to right-click and view image to be able to read it. Sorry
I probably got a bit too cavalier in some of my speculation, but I think there’s a lot to be learned about the author from this approach.
I’m pretty tired, having worked on this for the past few days without much break, so as much as I’d like to immediately provide what I would consider proper context to all of the points I find interesting regarding this data, I think I need to just take a break for a minute. I would really appreciate your feedback and insight, including criticisms of my premises and debunking of the observations in my commentary.
Also, nice to meet you. Thanks for all the hard work, keep it up.
EDIT 2: Also, I should have done this before but here’s a more accurate key
Also this is Double Gothic typeface that has been traced
Which was marketed as an font option by Royal Typewriters and is listed in the 1964 NOMDA Blue Book:
http://munk.org/typecast/wp-content/upl … yal-02.jpg
https://munk.org/typecast/2011/04/24/19 … nt-styles/
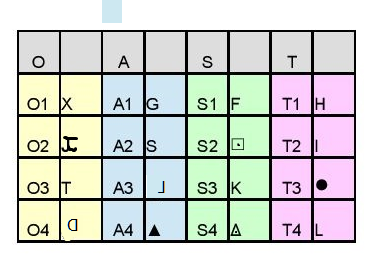
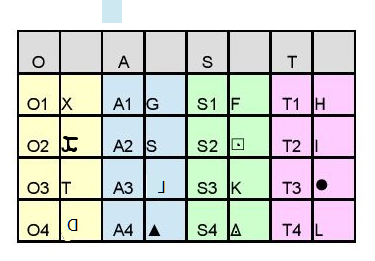
And if you take a look at the symbols OAST which had similar symbols in similar cycle positions in his key, you’ll notice this:
and I would think the anchor symbol makes it a bit of an outlier until I read about overstriking on a typewriter
https://en.wikipedia.org/wiki/Overstrike
And saw that you can make that symbol by overstriking T and J, and another J but in reverse, probably by flipping the paper over or using carbon paper in some way I haven’t fully thought through yet. Look where T and J are on that keyboard up there.
I’m not sure if this has been covered already.
EDIT: No I think this agrees very well with observations made in the past here regarding the QWERTY connection with homophone assignments. I’ll add a couple of things, though. First, I think it’s possible to figure out what his key actually looked like by charting the sequences of homophones and comparing them. I don’t think that this observation regarding the QWERTY connection was made by any contemporary source, so it’s entirely possible that he never even considered altering that part of his workflow. There might be a door into 340 with this kind of stuff, just maybe not a house on the other side.
I’m also not sold on polyphony when it comes to the 408 which has been suggested when it comes to triangular symbols. I think this guy just about broke his brain trying to finish this cipher and the only person he misled was himself when it came to his homophone substitutions.
I love this kind of analysis, but I’d say the G and U don’t match the font you show.
I think the cipher key link to keyboards is very interesting. Has anyone looked into teletype keyboards? Many had extra symbols depending on the type of service being done i.e. weather.
I love this kind of analysis, but I’d say the G and U don’t match the font you show.
I think the cipher key link to keyboards is very interesting. Has anyone looked into teletype keyboards? Many had extra symbols depending on the type of service being done i.e. weather.
You could be right. on the overtyping thing, though, there’s this:
There’s also the issue of single element vs. standard typewriter. In the former case, you can change the font. I think I read in the FBI files that they were having trouble identifying the model of typewriter because the sample size was too small. I haven’t found anything in depth on this topic (though I haven’t searched all of the forums). However, I do believe there was an identification of a Royal brand typewriter using Elite font (which is referred to as either Herald Elite or Royal Standard Elite in the NOMDA catalogue) made in connection with one or more of the letters.
EDIT: I did go through a god awful number of typefaces to try and debunk this connection. That’s not to say the research is exhaustive but I will note that most typefaces don’t have linear bars on their "Q" and I don’t think I came across a typeface where the center of the "M" did not reach the bottom of the symbol
I think over-typing is definitely interesting for the anchor symbol, but it is not uncommon to write a G or a U in exactly the same way as he has written it in the cipher.
I think over-typing is definitely interesting for the anchor symbol, but it is not uncommon to write a G or a U in exactly the same way as he has written it in the cipher.
Fair enough. It may not be all or nothing, though. Use of a typewriter would certainly make it easier to maintain consistent spacing between the columns and rows. I hope it doesn’t sound like I’m suggesting that the ciphers are typed and nobody looked into it. The FBI was concerned enough about the "concerned citizen" solution key to the 408 to test it for latent fingerprints* (I think the FBI tested it, but it might have been the Vallejo Police Department) which I’m assuming is why finding a Royal Elite typewriter in ALA’s house is something that they consider circumstantial evidence ("concerned citizen" was typewritten). I’m not sure but I get the feeling that they have serious concerns about the identity of whoever authored that key, which doesn’t mean that the Zodiac authored it. It might be that the substitutions in that key that don’t give the proper substitution might give them reason to believe that the author of "concerned citizen" might not have come to an independent solution, but instead authored the cipher and provided substitutions from his/her original key.
*SOURCE: https://vault.fbi.gov/The%20Zodiac%20Ki … 6%20./view
pages 31 and 32
Welcome to the forum Teg>Ean. I have to admit that I understand very little of what you are saying. Is it possible for you to list the points that you are making in a different way?
And if you take a look at the symbols OAST which had similar symbols in similar cycle positions in his key, you’ll notice this:
I don’t understand sorry.
Welcome to the forum Teg>Ean. I have to admit that I understand very little of what you are saying. Is it possible for you to list the points that you are making in a different way?
And if you take a look at the symbols OAST which had similar symbols in similar cycle positions in his key, you’ll notice this:
I don’t understand sorry.
*Sorry the image is too large to post here. I went ahead and added it to google drive: https://drive.google.com/file/d/1_shMpA … sp=sharing
Hey Jarlve,
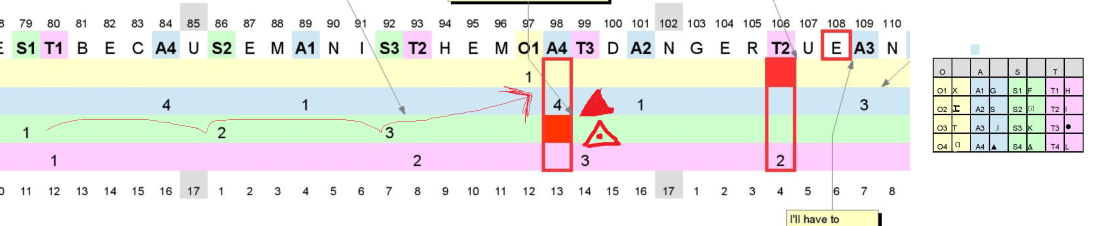
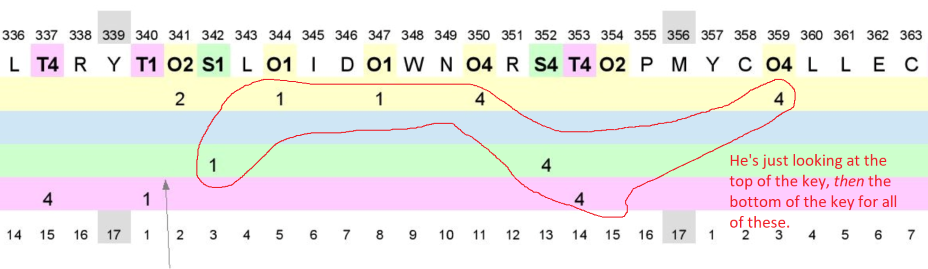
The premise is this: Since 408 has been solved, we know which plaintext letters have which symbol assignments. Because of this, we can go back to the 408 cipher and see the order in which each symbol appears in the cipher. We also know that there appear to have been mistakes with certain letters in the cipher [MOAT, MOAT, DANGERTUE, etc.]. So what I’ve done is picked four plaintext letters that were involved in some of these mistakes [O, A, S and T] and found where they first appear as substitutions in the cipher.
Then I wrote these symbols down in the order they appeared and, to help keep track of these symbols in the rest of the cipher, I labeled them according to the order in which they appear and the letter they correspond to.
Then I went through 408 and just replaced the symbols with these labels to make it easier to see if there were any relationships that popped out in the data and whether I could extrapolate anything about the mistakes that were made.
The image* I linked in my original post is basically like a timeline for each letter so that you can see where the author is at each moment in the text when it comes to the cycles for each symbol in his key for those four letters. It is based on the assumption that, in his key, he probably had each symbol listed one after the other, starting with the first one in his key and going through them sequentially as he made his substitutions. As it turns out, this assumption is pretty well supported by the data and, I would argue, illustrates pretty plausibly why he made the mistakes in the 408.
I annotated the crap out of it with observations I made and, in a few places, probably overreached with some of the deductions I was making, but that’s why I put it here; so that people can dispute or otherwise develop some of these observations and I can maybe get a better idea of what I’m looking at in the data.
It’s just another way of looking at the 408 that tries to put the mechanics of his encryption into sharper focus, a look under the hood if you will. As far as I was aware when I started, while similarities in some of the symbol assignments had been discussed as potential reasons why the author made his mistakes, the data had not been examined in this level of detail.
So that’s what I did. Let me know if you’d like me to clarify further or if you have any other questions/comments/criticisms, I’d appreciate the feedback.
EDIT: I would also like to do the same thing with the plaintext letters "I", "N" and possibly "R" but I’ve been looking into a different subject that relates to the 340 cipher and haven’t gotten to that yet (I have a lot of free time lately)
Thanks for explaining, it is clear now.
It is based on the assumption that, in his key, he probably had each symbol listed one after the other, starting with the first one in his key and going through them sequentially as he made his substitutions. As it turns out, this assumption is pretty well supported by the data and, I would argue, illustrates pretty plausibly why he made the mistakes in the 408.
I suppose that most people would do it this way so that makes sense. Can you go into more detail as to why the data supports it? I’m sorry but trying to figure out the 16K image just kills my brain. ![]()
Did you made other observations of note?
What is the image "OAST distribution on keyboard" about? I don’t get it.
Thanks for explaining, it is clear now.
It is based on the assumption that, in his key, he probably had each symbol listed one after the other, starting with the first one in his key and going through them sequentially as he made his substitutions. As it turns out, this assumption is pretty well supported by the data and, I would argue, illustrates pretty plausibly why he made the mistakes in the 408.
I suppose that most people would do it this way so that makes sense. Can you go into more detail as to why the data supports it? I’m sorry but trying to figure out the 16K image just kills my brain.
Did you made other observations of note?
Because the only reason he didn’t substitute homophones in a perfectly cyclical manner is that he mixed the key for one letter with the key for another letter, but the reason he did that is that he was expecting the substitution anyways.
Also, you can see in the third part exactly how he gave up on the cycles because he just couldn’t take it anymore.
I’m not sure how comfortable he was with what he was doing. Best to be careful to not extrapolate with the safety off, but this says a lot.*
*He’s putting all this effort into something that doesn’t do anything but make it easier for the code to be broken.
Because the only reason he didn’t substitute homophones in a perfectly cyclical manner is that he mixed the key for one letter with the key for another letter, but the reason he did that is that he was expecting the substitution anyways.
I see now, A4 and S4, MOAT, MOST. And T2 and O2. I never realized these errors were this obvious. Say that his key was indeed a vertical table, how did he jump all the way from A to S etc? That must have meant that his key table was ordered by frequency, number of homophones? I am guessing that you already inferred that somewhere on your documents? Very interesting!
He’s just looking at the top of the key, then the bottom of the key for all of these.
By your chart I counted the 1234’s for the last 408 part, they are 13 x 1, 8 x 1, 8 x 3 and 9 x 4. That seems like a normal random distribution to me. I am not sure that this is what happened here.
By your chart I counted the 1234’s for the last 408 part, they are 13 x 1, 8 x 1, 8 x 3 and 9 x 4. That seems like a normal random distribution to me. I am not sure that this is what happened here.
I think you’re right. I think his process falls apart on him at the end. He might have been in a rush, which is why it makes sense to me that it was more important to fill all of the space, make all the parts equal in size, than the actual content of the message. While I’m not married to the idea, I could buy the idea that, were it not for these mistakes in the encryption, the plaintext might have actually been grammatically correct.
I might take a look again at the actual cipher tomorrow or soon because one of the other things I’m wondering is whether, in the last part, he was copying substitutions from the cipher as he was writing it rather than consulting his key (hence concurrent substitutions of the "L" symbol).
This may not seem like an issue that has any importance, but I’m curious as to whether he wrote the three parts separately or whether it was on a single sheet he cut into three pieces after completing the cipher. It might be possible that he wrote his key on the same sheet when it was all together then cut it off before he noticed any issues with the third section. If he messed it up the first time, he might have had to redo the encryption on that last part which could explain why he didn’t make any typos except for all that junk at the end.
By the way, you asked about the keyboard thing. I honestly just found it interesting that these three letters might have been next to each other on the key and next to each other on a keyboard. And it’s also because I’m seeing a lot of things that might be relevant to this topic in the 340.
Here’s the original post about someone making the keyboard observation:
I adapted the observation into this image for a presentation:

It’s an interesting observation. I wonder if the keyboard layout really did play a role in him making the cipher key. It’s hard to tell since a lot of the key doesn’t seem related to the layout.
This looks interesting but I’m too dumb to understand.
Are you saying Zodiac:
1. Made all his characters on a typewriter?
2. Chose his substitutions based on the standard keyboard arrangement?
3. Typed up his cipher while looking at a separate key?
4. This separate key was oriented vertically, but not A-Z. Rather he had the alphabet in order of the letters with the greatest number of substitutions?
Sorry I’m lost.